CloudBees Pipeline Template Catalogs
Up to this point, the Jenkinsfile that we have created has grown and provides an overview of some important declarative pipeline concepts, but it does not do a whole lot. In this lab we will explore how pipeline templates, provided by the CloudBees CI Pipeline Template Catalog feature, are able to accelerate your continuous integration by providing ready-to-go, full featured pipelines.
Pipeline Template Catalogs provide version controlled, parameterized templates for Multibranch and stand-alone Pipeline jobs. In this lab we will use a template from a Pipeline Template Catalog to create another Multibranch Pipeline project for your copy of the insurance-frontend repository. However, the Jenkinsfile will be pulled from your pipeline-template-catalog repository instead of from your insurance-frontend repository. But the source code that the pipeline template executes upon will still be checked out from your insurance-frontend repository.
Creating Pipeline Jobs from Pipeline Templates
Creating a new job from a catalog template is as simple as filling in a few template specific parameters or by adding a simple yaml based job configuration to your controller’s configuration as code bundle. After that, you will have an organization tested Pipeline for the insurance-frontend application with all the same benefits as a non-templatized Multibranch pipeline project. Also, note, that although everyone is using a template from their copy of the pipeline-template-catalog repository, we could just as easily have everyone use a template from the same repository.
- Navigate to the top-level of your CloudBees CI managed controller and click into the pipelines folder, and then click on New Item in the left menu. Make sure you are in the pipelines folder.
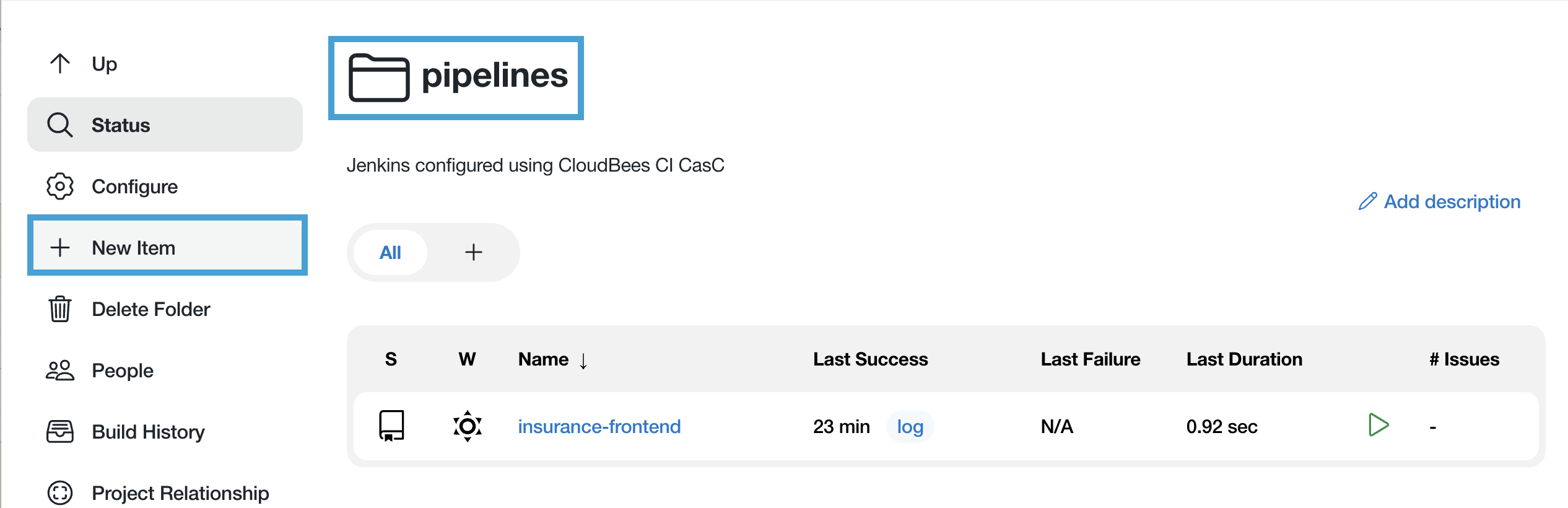
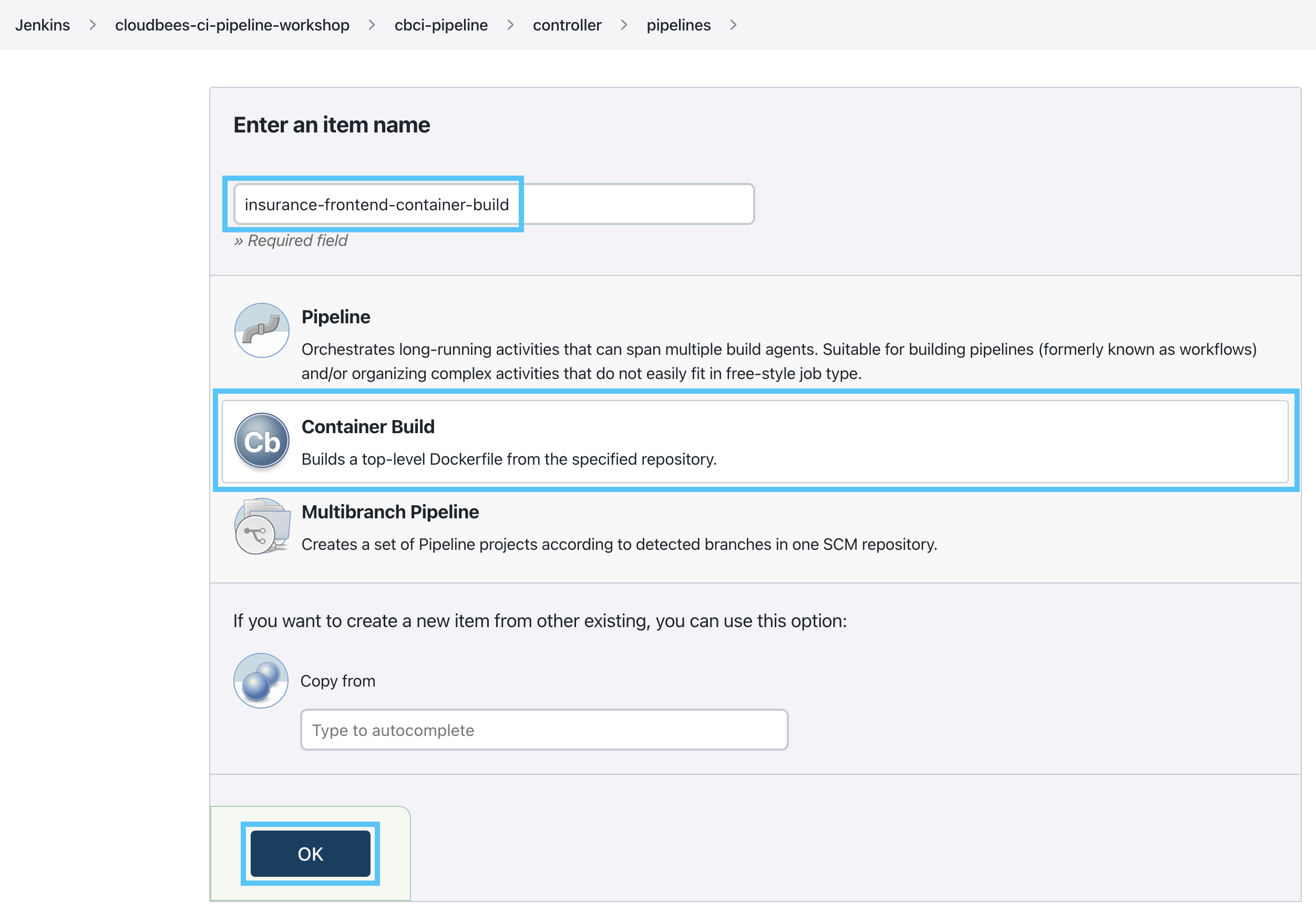
- Enter insurance-frontend-container-build as the Item Name and select Container Build as the item type and click the OK button.
- On the next screen, all of the pre-configured values should be correct. So all you have to do is click the Save button.
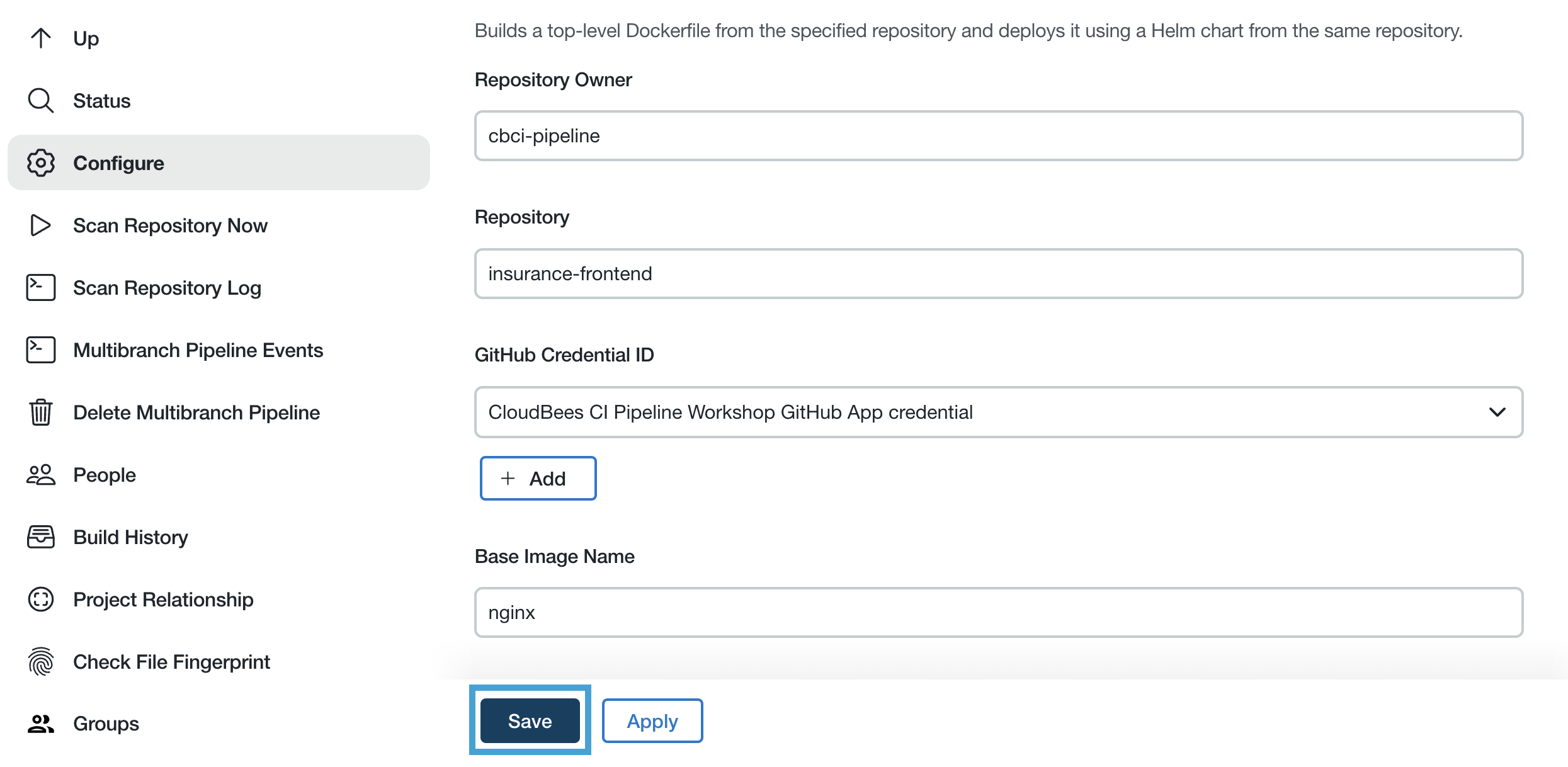
The Repository Owner parameter will match the GitHub Organization that you are using for the workshop; not what is in the screenshot above.
- After you click the Save button, the Multibranch Pipeline project (created by the template) will scan your
insurance-frontendrepository, creating a Pipeline job for each branch where there is a marker file that matchesDockerfile(or in this case, themainbranch).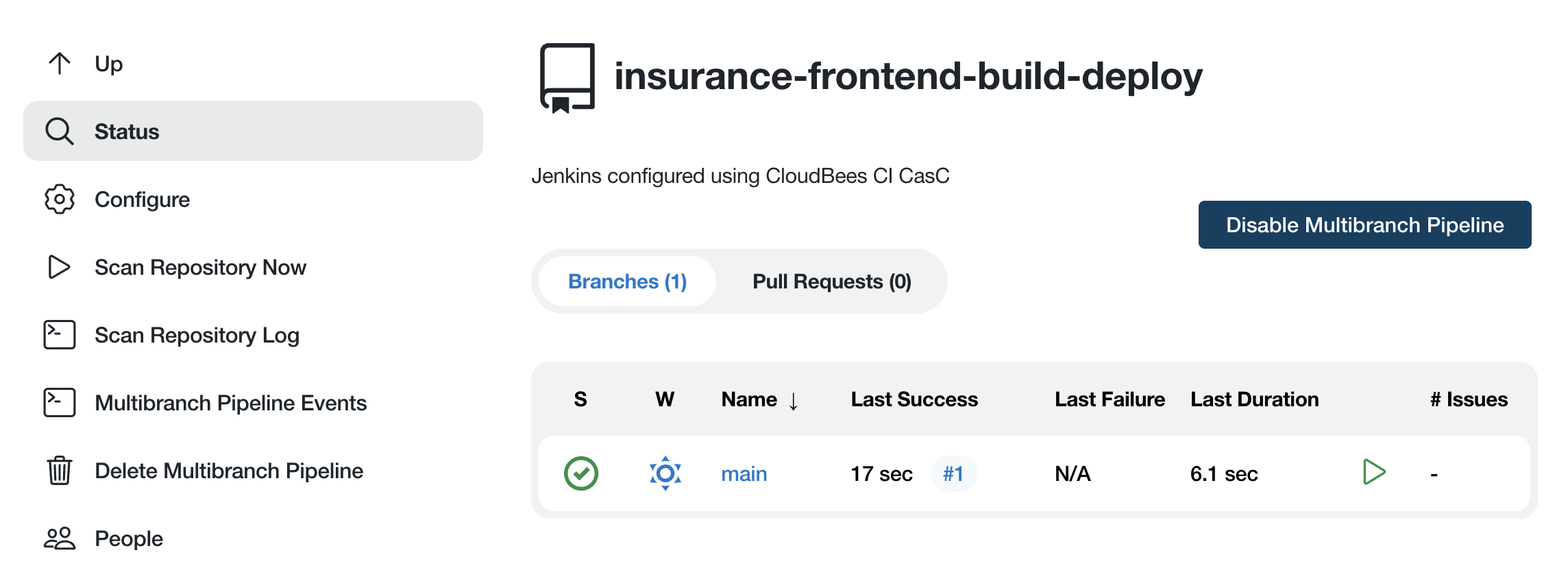
- The marker file and parameters of a catalog template are defined in a
template.yamlfile that is stored alongside aJenkinsfilewithin a subfolder of the Pipeline Template Catalog required top-leveltemplatesfolder. The name of the subfolder will be used as an internal identifier of the template so it is recommended to keep it all lowercase with no spaces. Navigate to thetemplate.yamlfile under/templates/container-buildin your copy of thepipeline-template-catalogrepository and you will see a file similar to the one below:
version: 1
type: pipeline-template
name: Container Build
templateType: MULTIBRANCH
description: Builds a top-level Dockerfile from the specified repository.
parameters:
- name: repoOwner
type: string
displayName: Repository Owner
defaultValue: REPLACE_GITHUB_ORG
- name: repository
type: string
displayName: Repository
defaultValue: insurance-frontend
- name: githubCredentialId
displayName: GitHub Credential ID
type: CREDENTIALS
defaultValue: cloudbees-ci-pipeline-workshop-github-app
multibranch:
branchSource:
github:
id: container-image-build
credentialsId: ${githubCredentialId}
repoOwner: ${repoOwner}
repository: ${repository}
traits:
- gitHubBranchDiscovery:
strategyId: 1
- gitHubPullRequestDiscovery:
strategyId: 1
markerFile: Dockerfile
- The
REPLACE_GITHUB_ORGdefaultValuefor therepoOwnerparameter has been replaced with the name of your workshop GitHub Organization in your copy of thetemplate.yamlfile for yourcontainer-buildtemplate. Note also that thetemplateTypeisMULTIBRANCHand there is amarkerFileconfigured with the value ofDockerfile. - You may have noticed that none of the
stagesare executed for themainbranch job. Navigate to theJenkinsfilein the samecontainer-buildsubfolder (under thetemplatesfolder) of your copy of thepipeline-template-catalogrepository, and you will discover why. The contents should match the screenshot below: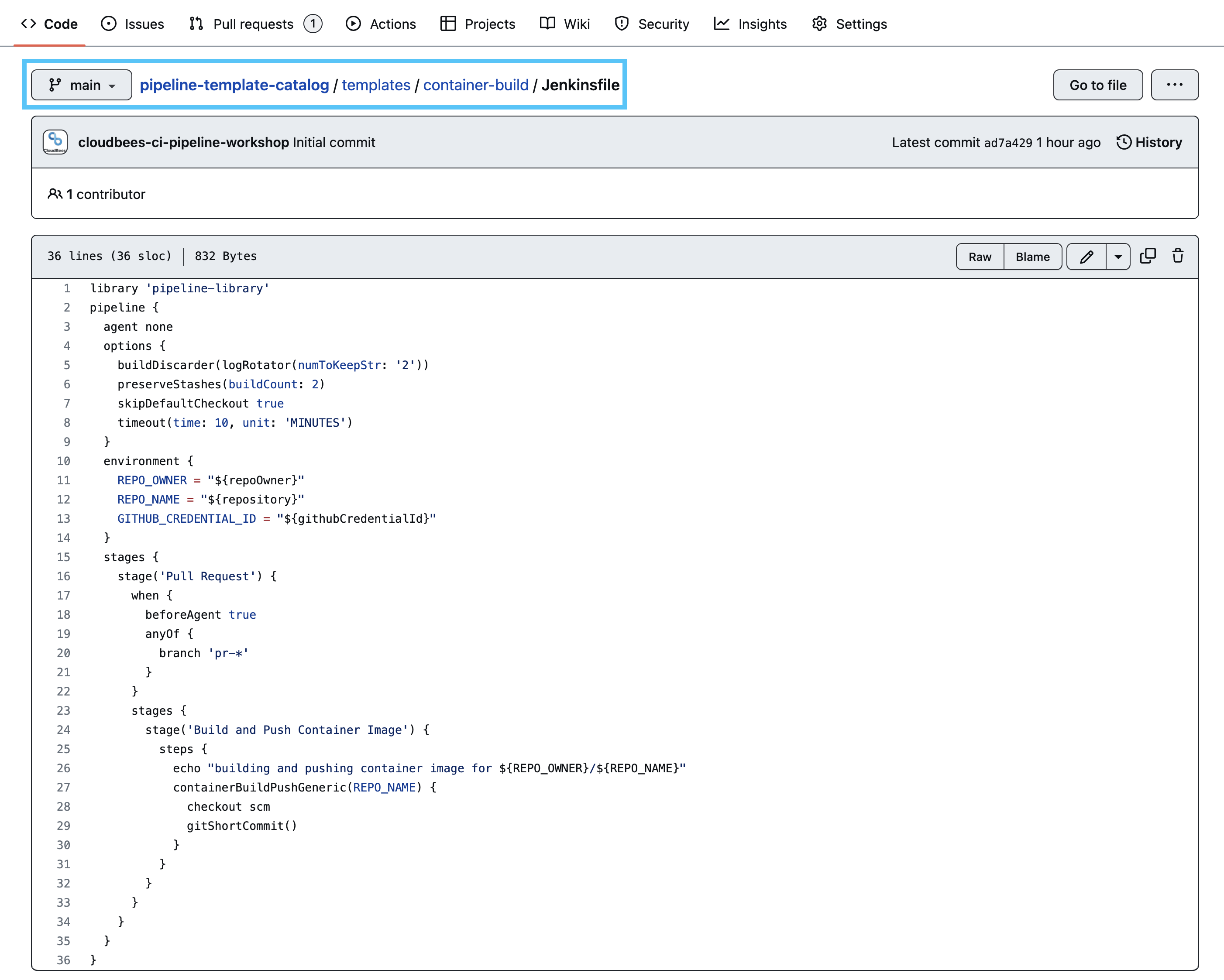 Some of the highlights include:
Some of the highlights include:
- On line 1 we are importing a Pipeline Shared Library that allows us to share custom steps between multiple pipeline definitions - templates or not.
- On line 3 we declare
agent noneas we don’t want to spin up an agent if thewhenconditions are not satisfied. - On line 7 the
skipDefaultCheckoutoption is set totrueto disable the automatic checkout of source code in every Declarative Pipelinestage, since we only need to checkout the source code in onestage. - On line 10 we define global environment variables. These will be available in all subsequent
stagesof the pipeline, even nestedstages. - On line 17 a
whencondition is defined that will only allow the Staging PR nestedstagesto be executed when thebranchbeing processed is a GitHub pull request. This is why nostageswere executed for themainbranch. - On line 28 we are calling the
containerBuildPushGenericPipeline Shared Library global variable that provides a common, repeatable method for building and pushing Docker images. (In this case we are building and pushing container images with a tool called Kaniko which allows building and pushing container images from a Kubernetespodwithout Docker installed.) - On line 29
checkout scmis called so thecontainerBuildPushGenericglobal variable step will have access to theDockerfileand application code of yourinsurance-frontendrepository. We must explicitly call this as we disabled the Declarative Pipeline default checkout in the globaloptionsblock above.
- Now we will create a pull request in your copy of the
insurance-frontendrepository. Navigate to themainbranch of your copy of theinsurance-frontendrepository and click on theJenkinsfile. - We are going to delete this
Jenkinsfilesince we will now be using theJenkinsfilefrom the Container Build catalog template. Click on the trashcan icon at the top of the file, again ensuring that you are on themainbranch.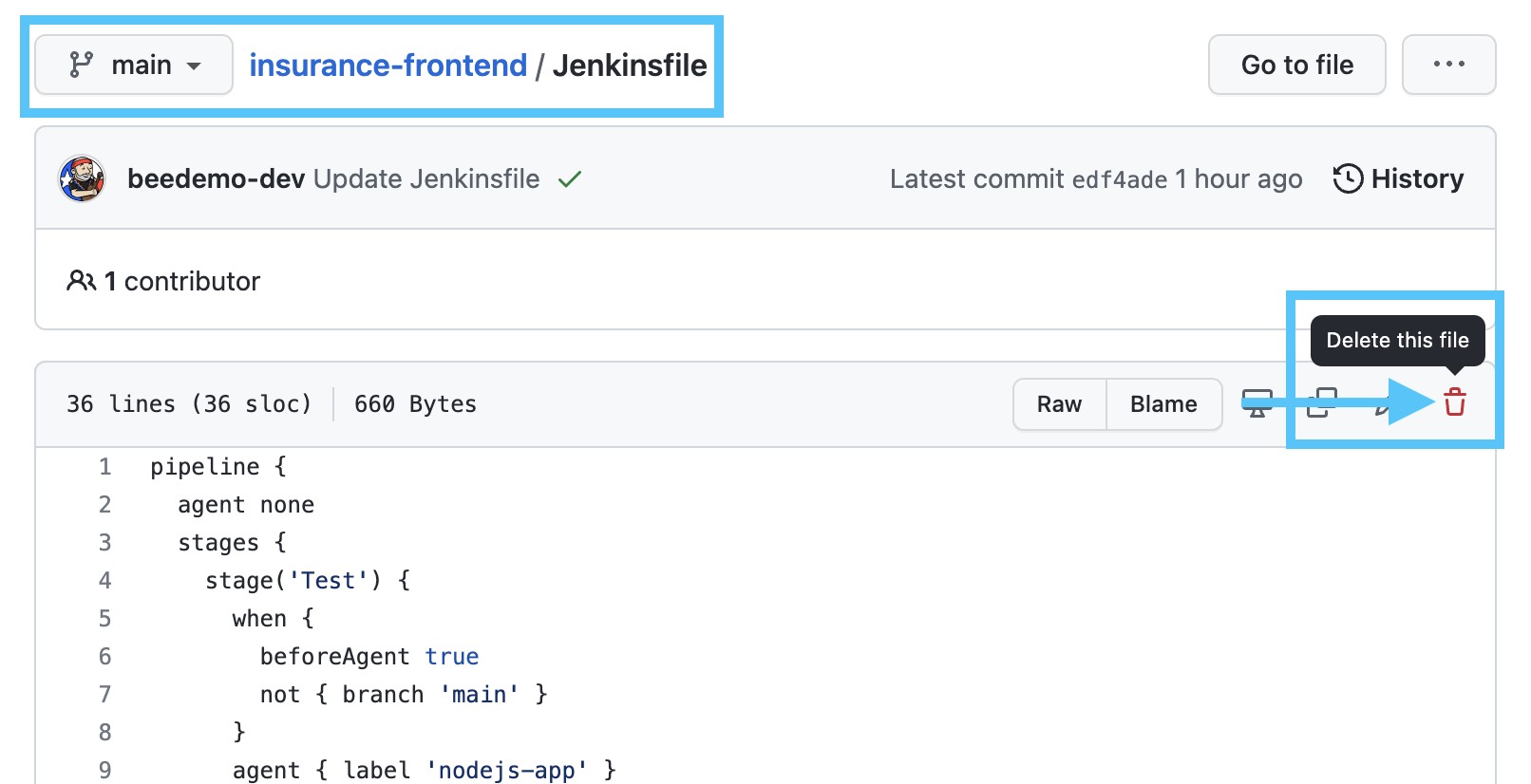
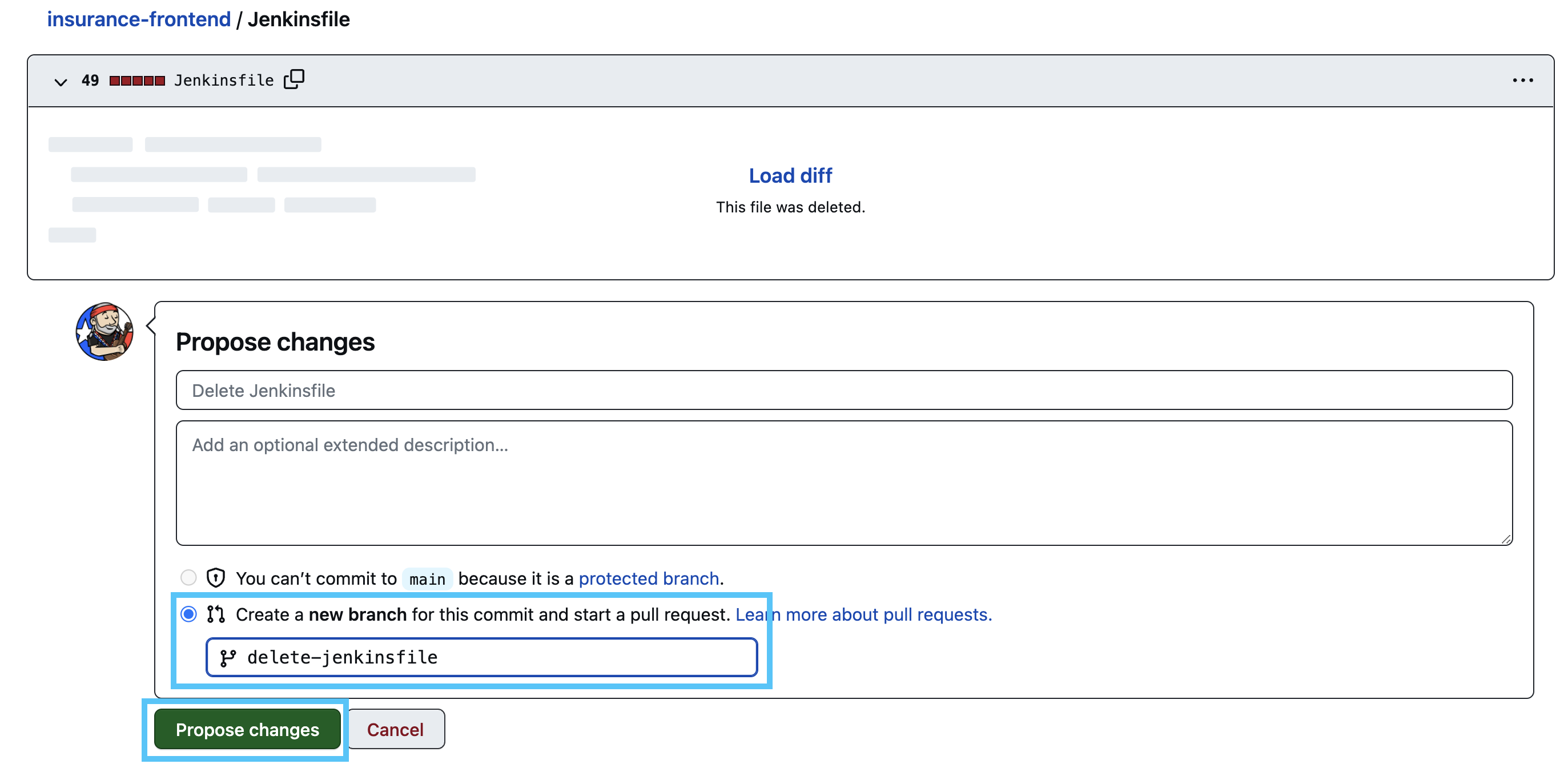
- On the next screen, make sure that Create a new branch for this commit and start a pull request., name the new branch delete-jenkinsfile and click the Propose changes button.
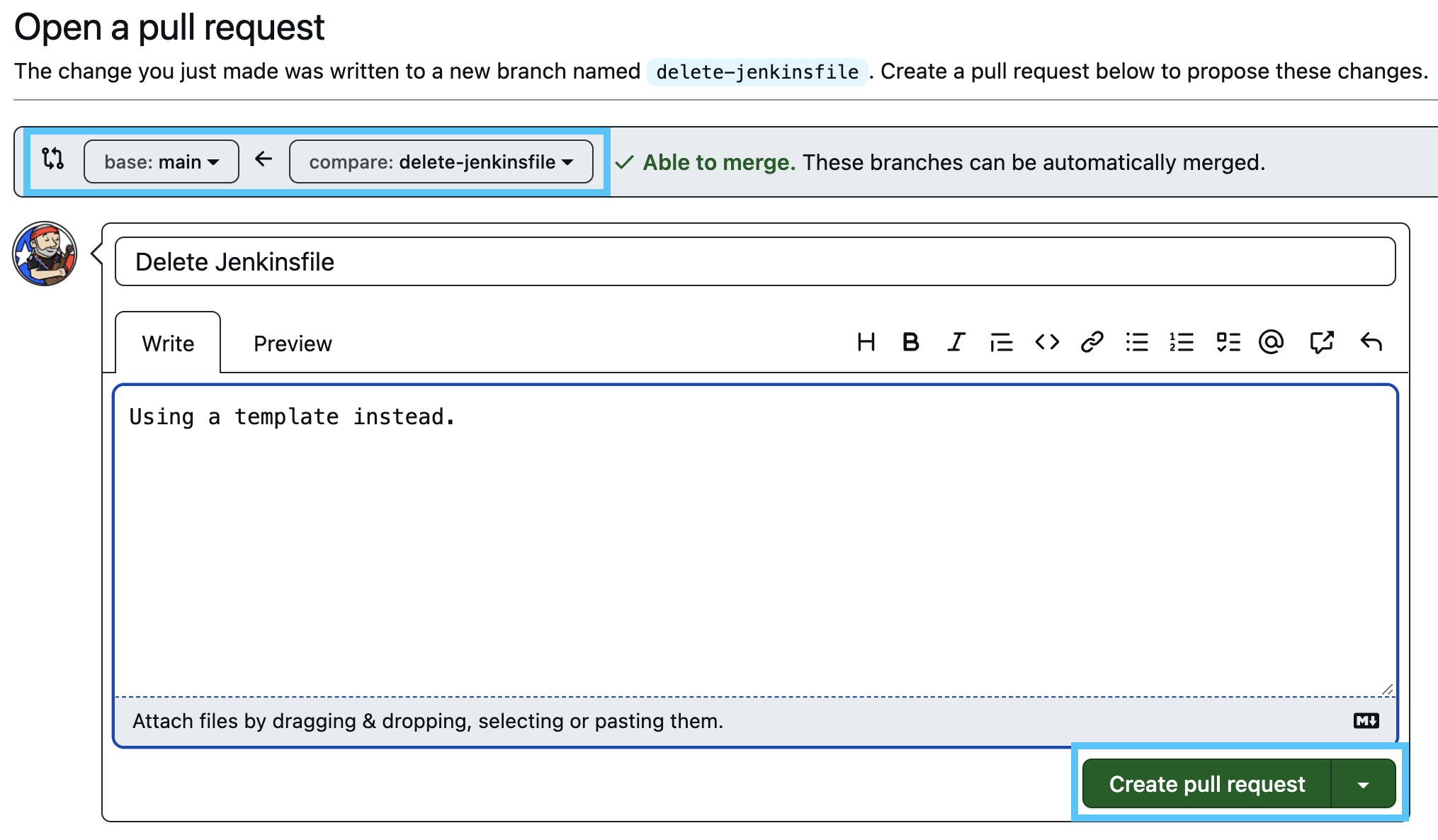
- On the next screen, click the Create pull request button.
- Navigate to the insurance-frontend-container-build job on your controller and you will see that there is a new Pull Requests job (you may need to refresh the page).
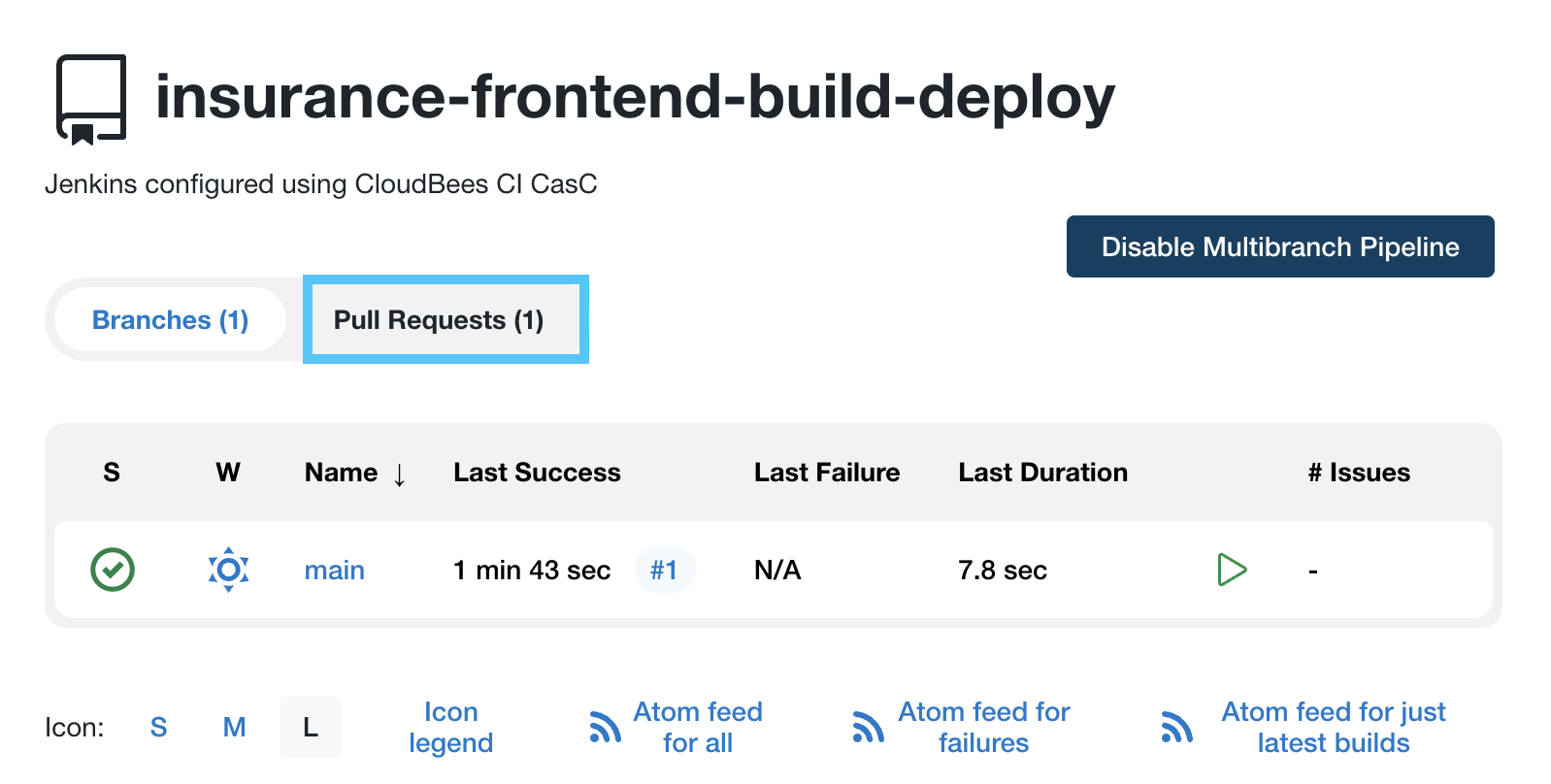
- Click on the Pull Requests tab and you should see a PR job running.
- It will take the job a few minutes to complete as it is utilizing a multistage Docker build in the
Dockerfilethat will build theinsurance-frontendapplication from the source code checked out from your copy of theinsurance-frontendrepository and then creates a runtime container image that is pushed to a Google Cloud Artifact Registry via thecontainerBuildPushGenericPipeline Shared Library global variable step. IMPORTANT: Do not merge the pull request!
Ephemeral Deployment Environments for Pull Requests
In this section we are going to provide a brief overview of CloudBees Previews - a standalone feature of CloudBees CI that is currently in preview. Although this is not Jenkins pipeline specific, it does allows us to easily provide preview environments for a GitHub pull request without any additional pipeline code. In previous versions of this workshop we used the following Jenkins pipeline shared library step to providing a staging environment for GitHub pull requests:
def call(String name,
String imageTag,
String namespace = "staging",
Closure body) {
def label = "helm-${UUID.randomUUID().toString()}"
def podYaml = libraryResource 'podtemplates/helm.yml'
podTemplate(name: 'helm', inheritFrom: 'default-jnlp', label: label, yaml: podYaml, podRetention: never(), activeDeadlineSeconds:1) {
node(label) {
body()
stagingUrl = "https://${name}.${env.DEPLOYMENT_ENV}.workshop.cb-sa.io"
gitHubDeploy(REPO_OWNER, REPO_NAME, "", "staging", GITHUB_CREDENTIAL_ID, "true", "false")
env.NAME=name
env.IMAGE_TAG=imageTag
env.NAMESPACE=namespace
container('helm') {
withCredentials([string(credentialsId: 'fm-key', variable: 'FM_KEY')]) {
sh '''
helm upgrade --install -f ./chart/values.yaml --set image.tag=$IMAGE_TAG --set fmToken=$FM_KEY --namespace=$NAMESPACE $NAME ./chart
'''
}
}
gitHubDeployStatus(REPO_OWNER, REPO_NAME, stagingUrl, 'success', GITHUB_CREDENTIAL_ID)
//only add comment for PRs - CHANGE_ID isn't populated for commits to regular branches
if (env.CHANGE_ID) {
def config = [message:"${env.DEPLOYMENT_ENV} environment deloyed by CloudBees CI and is available at: ${stagingUrl}"]
gitHubComment(config)
}
}
}
}
In addition to the additional pipeline code, we also had to manage the configuration and cleanup of environments in the Kubernetes cluster we are using for the workshop. CloudBees Previews eliminates the need for both.
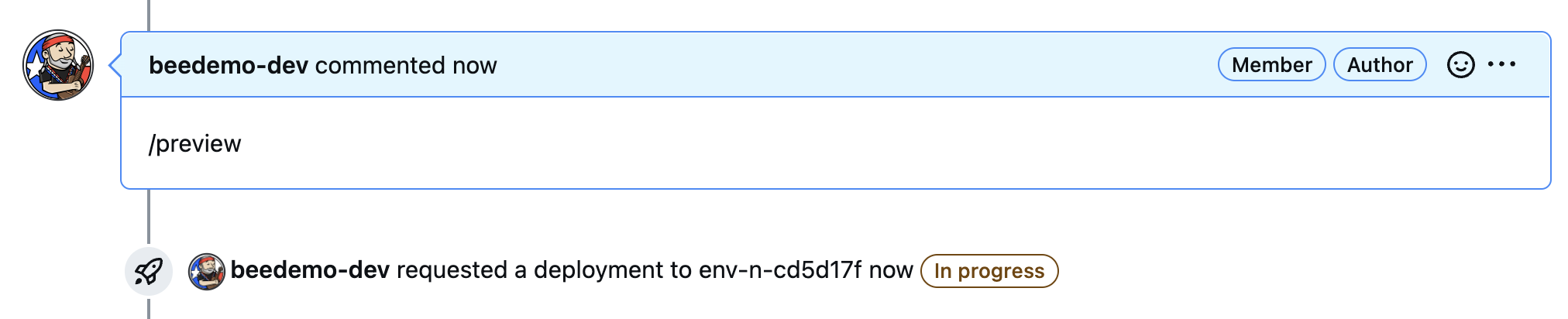
- Once the PR job has completed, navigate to the corresponding open pull request in your copy of the
insurance-frontendrepository. Make sure you are on the Conversation tab, scroll down to the comments, enter /preview and click the Comment button. - you should see a notice that you have requested a deployment under your comment and that it is In progress.
- After a minute or so you should see a message stating: “This branch was successfully deployed”. Click on the Show environments link in that block and then click on the View deployment button.
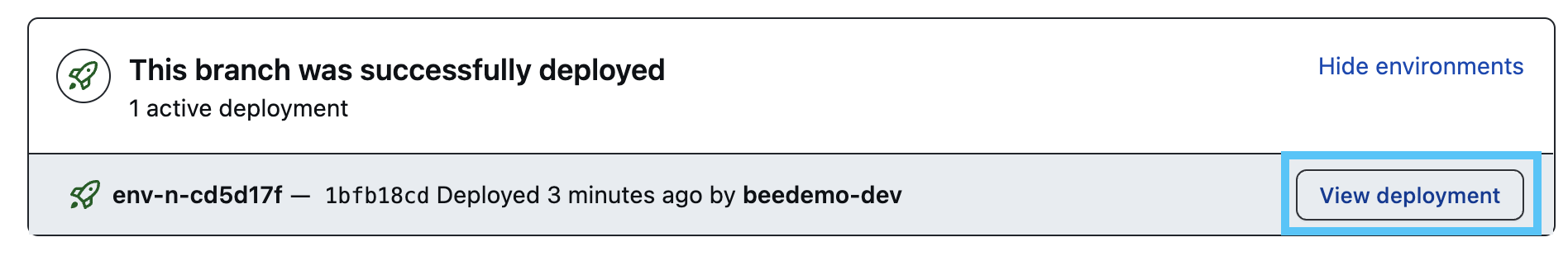
- Navigate back to the Delete Jenkinsfile pull request in your copy of the insurance-frontend GitHub repository. Ensure that you are on the Conversation tab and scroll down, click the Merge pull request button and then the Confirm merge button.
- After a few seconds, refresh the tab with your pull request preview environment and it should be gone. As soon as a pull request is closed, CloudBees Previews will destroy all environments associated with that pull request.